Privacy Impact Assessment
Stichting Onderzoek Marktinformatie (SOMI)
Amstelveen, Nederland
9 November 2021
Part 1 – Context
1.1 Overview
What is the processing under consideration?
Stichting Onderzoek Marktinformatie (“SOMI”) has launched SOMI app since October 2020. Via this app, SOMI assists users in exercising their privacy rights as referred to in Article 15 up to and including Article 20 of the General Data Protection Regulation (“GDPR”). In case of a violation of the GDPR, SOMI represents the data subject in exercising the rights referred to in Articles 77, 78, 79 and 82 GDPR, which representation is based on Article 80 GDPR.
The SOMI application allows users to request their personal data from any organisation in the EU and EEA that processes their personal data. The app also allows users to have their personal data deleted via SOMI or to have their data assessed for violation of the GDPR. Users can also (anonymously) report privacy violations with SOMI, such as loss, theft or illegal handling of personal data, non-transparent use of personal data, etc. Furthermore, users can join collective actions. By joining such action, the user allows SOMI to act on their behalf when an organisation violates the GDPR. Depending on the violation and the company, SOMI can file for compensation and/or obtain information of the GDPR violations with regard to the users. At this moment, users can join collective actions against TikTok, Zoom and Palantir. The anticipated compensation per person is EUR 500.-
In representing its users, SOMI requires users to register and provide their personal data. To make sure that SOMI is acting on behalf of the entitled person, SOMI asks for a copy of the ID of the user.
The app also allows data processing entities to contact SOMI with regard to GDPR issues, enabling the organisation to be efficiently GDPR compliant. Organisations can fill in a contact form for that purpose.
What are the responsibilities linked to the processing?
SOMI is the data controller of SOMI app. SOMI is a Netherlands-based non-profit organisation established to identify and influence issues of social importance. SOMI focuses on the functioning of markets in the areas of privacy, elderly, housing and care.
Dotswan B.V., Stichting De Bewaarder, GetID and Hetzner Online GmbH are data processors for SOMI.
Dotswan B.V. and Stichting de Bewaarder process analytical data about activities in the app in order to improve the functionalities and user interface.
GetID processes identification data necessary to verify the users.
SOMI’s server infrastructure is hosted by Hetzner. However, Hetzner does not have access to any data, as it was hosted on our own VPS server.
Are there standards applicable to the processing?
SOMI has implemented several organisational and administrative policies and controls such as risk assessments, internal audits, an information security policy, training of staff, (security) incident and data breach management procedure. SOMI has also appointed an independent Data Protection Officer certified by the Data Protection Institute BVBA. In addition to adherence by controllers or processors to the GDPR, appropriate measures were established regarding:
(a) fair and transparent processing;
(b) the legitimate interests pursued by controllers in specific contexts;
(c) the collection of personal data;
(d) the pseudonymisation of personal data;
(e) the information provided to the public and to data subjects;
(f) the exercise of the rights of data subjects;
(g) the information provided to, and the protection of, children, and the manner in which the consent of the holders of parental responsibility for children is to be obtained;
1.2 – Data, processes and supporting assets
What are the data processed?
The categories of data processed are different between the consumer users and the data processing entity users.
I. Consumer users
The following data from consumers is collected and processed:
- Account information (email address, password, account number) collected when the user creates an account;
- Personal and contact information (first name and last name, gender, address, phone number, email address);
- Personal identification information (copy of ID card) and information on the ID card (nationality, gender, date of birth, place of birth, issue and expiration date, place of issue, etc.) in order to represent and exercise the rights of data subjects;
- Payment information and relevant data in relation to the provision of the services and/or data to manage user rights (bank account number, user agreements, statements, contracts, etc.);
- Analytical data about activities using the app (login timestamp, IP address, tabs accessed, time spent, language, etc.);
- Data provided by third parties when the data subjects explicitly requests SOMI to exercise his/her rights;
- Information about the data collected from third parties when the data subjects explicitly asks of to perform analysis of the data provided;
- Data concerning privacy violations reported through the app (first and last name, email address, phone number, content of the report and whether the report is anonymous (in that case, the subject’s name will not be provided to the data processing entities and supervisory authorities));
- Meta data regarding the rights the user has exercised;
- Other data that the data subjects actively provide to us, for example, correspondences, support requests and messages to SOMI.
II. Data processing entity users
The following data from data processing entities is collected and processed:
- Company name or Chamber of Commerce number;
- Website;
- Contact request;
- Email address;
- Phone number;
- Content from ‘Anything else’ field;
- Option to subscribe to newsletter.
III. Storage term
The following storages terms apply:
- Data regarding activities on the app and will be stored for a maximum of 12 months;
- Contact information and data that data subjects actively provide to SOMI will be stored for a maximum of 36 months after the last contact between the data subject and the data controller;
- Personal identification data (copy of ID or passport) will be stored for a maximum of 36 months after the last contact between the data subject and the data controller;
- Contracts, data regarding payments and invoices are stored 10 years in order to comply with SOMI’s legal responsibilities;
- All personal data collected from third parties will be deleted at the simple request of the user or ultimately after the expiration of the user account (after 36 months of inactivity).
- All the data except for contracts and data regarding payments and invoices will be immediately deleted after the deactivation of the user account or after 36 months of inactivity.
IV. Access
- The following persons have access to the abovementioned data: Only SOMI’s security engineer and technical support staff with GDPR knowledge and the abovementioned data processors will have access to the data.
- All data collected from third parties will be automatically encrypted when processed. Any further processing will require the data subject to provide a unique password;
How does the life cycle of data and processes work?
I. Data collection
a) Customer users
To create an account, a user must register and follow the registration process. Required data: first name, last name, email address, password, referral (Google, Facebook, friend, other).
After registration the user receives an email to confirm the account. This message also appears on the dashboard in the app. When the user confirms the account, the user receives a request at the top of the screen to confirm his/her identity. If the user clicks on it, the ID Verification page appears.
When confirming the identity, the user must upload an identification document, which can be an ID or a passport. The following data are also requested: country, date and place of birth, document number, expiration date, issue date and place of issue of document.
In addition, other profile data can be entered at Settings, such as telephone number, language and address, and email and gender. The user can also upload an avatar as an image.
Next to Settings, there is a tab with My Info. There the user can see their information such as: name, email, mobile, last login, gender, referral, newsletter status.
After the ID verification data has been entered, the ID will be verified by SOMI (status 'Pending'). SOMI will subsequently act on behalf of the user in submitting a request with the data processing entity.
When a violation of the GDPR is found, SOMI can contact the data processing entity in order to remedy the violation, file a complaint with the supervisory authority or start a collective action. SOMI may ask for a signature of the user in case of filing a complaint or starting a collective action.
Finally, the user has the option to report a privacy violation. The data required is name, email address, phone number, content of the report and option to report anonymously. SOMI analyses those data to determine whether the violation has occurred, and whether further legal actions should be taken accordingly.
b) Data processing entity users
Data processing entity users were asked to fill in their contact information such as name of the company, commercial registration number, website, phone number and they can specify their request in the ‘anything else’ field. SOMI will reach out to the organization via the email/phone call, however the app will be used to notify the data processing entity users of the updates and provide timeframe for them to fulfil the GDPR requests.
II. Data destruction
- Data regarding activities on the app and will be deleted after 12 months;
- Contact information and data that data subjects actively provide to SOMI will be deleted for the maximum of 36 months after the last contact between the data subject and the data controller;
- Personal identification data (copy of ID or passport) will be deleted for the maximum of 36 months after the last contact between the data subject and the data controller;
- All personal data collected from third parties will be deleted at the simple request of the user or ultimately after the expiration of the user account or after 36 months of inactivity.
- All the data except for contracts and data regarding payments and invoices will be immediately deleted after the deactivation of the user account or after 36 months of inactivity.
What are the data supporting assets?
SOMI’s own database (my.somi.nl) and Zoho cloud software suite. The hardware is secured by supplier ContinYou in Gennep, The Netherlands. Continyou installed a security system on SOMI’s Windows computers (SentinalOne).
Evaluation: Acceptable
Part 2 – Fundamental principles
2.1 Proportionality and necessity
Are the processing purposes specified, explicit and legitimate?
SOMI processes personal data for the following purposes:
- Provide its users a simple and convenient way to exercise their rights accordingly with the GDPR (as referred to in Articles 15, 16, 17, 18, 19 and 20 of the GDPR);
- Verify its users’ identities in order to execute agreements on behalf of the subject in which SOMI represents (as referred to in Articles 77, 78 and 79 of the GDPR);
- Development process and to improve the functionality and user interface of the app;
- Correspond with users in relation to support;
- Promote, inform, educate and advise consumers of their rights to privacy and data protection;
- Identify and investigate suspected GDPR violation from digital services and platforms operating in the EU and EEA via the submissions from consumers;
- Take subsequent legal actions such as collective action and official complaint letters when the violation has been found, claim compensation for the injured parties (as referred to in Article 82 of the GDPR);
- Assist data processing entities by identifying the possible GDPR violation and handover the subject access request or erase request on behalf of consumers;
Evaluation: Acceptable
What are the legal basis making the processing lawful?
SOMI processes personal data on the basis of the following principles:
- Identification data, account information and data collected from third parties are always processed on the basis of the informed and explicit consent of the data subject. The user may withdraw their consent at any time. This withdrawal does not affect the legitimacy of the processing before the withdrawal, but from the moment the data subject withdraws their consent, the personal data will no longer be processed;
- Functional and analytical data about the behavior of data subjects in the app are processed on the basis of the legitimate interest of our organisation. This data does not have an impact on the privacy of user, as it cannot be used to differentiate or identify individuals;
- Data necessary to be able to provide goods and services such as authorization letter and signature are collected where necessary for the performance of a contract or in order to take steps at the request of the data subject prior to entering into a contract;
- Identifications (e.g. copy of ID or passport) are processed as it is strictly necessary for the establishment, exercise or defence of rights and legal claims;
- Certain data about payments, invoices, agreements, statements, etc. are kept for a longer period of time in order to comply with tax and anti-money laundering legislation;
The App does not aim to process special categories of personal data, such as data revealing racial or ethnic origin, political opinions, religious or philosophical beliefs, or trade union membership, and the processing of genetic data, biometric data for the purpose of uniquely identifying a natural person, data concerning health or data concerning a natural person's sex life or sexual orientation.
However, when the data subject requests SOMI to collect data from third parties, it could happen that such data is processed by SOMI. Therefore, such data will only be processed based on the explicit consent of the data subject to the processing this data for the specified purpose of exercising his/her rights as a data subject. Given this circumstance, the data subject should be fully aware that specific personal data are being processed.
If analysis reveals such special categories of data are being processed, the user will be given the option of permanently deleting these categories of data.
Evaluation: Acceptable
Are the data collected adequate, relevant and limited to what is necessary in relation to the purposes for which they are processed?
- Functional data and analytical data related to activities in the App are strictly necessary in order to create a functional and user-friendly interface for the data subject;
- Contact information and data that the users actively provide to SOMI are strictly necessary in order to communicate with the user regarding functionalities of the app and to provide support whenever requested;
- Personal identification information (e.g. copy of national ID card) will be collected in order to exercise the rights of data subjects and to represent the data subjects in legal actions;
- Payment information (such as bank account name and number), contracts, invoices and related data are strictly necessary in order to provide goods and services to the data subjects. In order to comply with tax and anti-money laundering legislation some data must be kept for a longer period of time;
- Meta data regarding the rights the user has exercised is strictly necessary in order to exercise the rights of data subjects and to create a functional user experience;
- Data provided by third parties and any analysis of this data will only be processed when the user explicitly requests SOMI to do so. In this circumstance, the data subject is fully aware that specific personal data are being processed. This data will only be collected whenever strictly nessessary in order to exercise the rights of the data subjects.
Evaluation: Acceptable
Are the data accurate and kept up to date?
Data provided by the data subjects were periodically reviewed and kept up to date. If attributes have expired, they need to be refreshed by the user. Identification data such as copy of ID and passport were validated by GetID, to ensure that the user’s identity is real and also to deduplicate the data. Data provided by third parties will only be reviewed on the basis of the explicit and informed consent of the user. SOMI is therefore not responsible for the quality or accuracy of the data provided by third parties.
Evaluation: Acceptable
What are the storage duration of the data?
The maximum period the data will be stored:
- Data regarding activities on the app and will be stored for a maximum of 12 months. This period is justified in order to make annual statistics and periodically review the workflow of the App;
- Contact information and data the data subjects actively provide to us will be stored for a maximum of 36 months after the last contact between the data subject and the data controller. This period is justified in order to engage with data subjects regarding any queries and/or follow up any support questions. After 36 months of inactivity (and several notifications) the account and collected personal data will be automatically deleted;
- Personal identification data (copy of ID or passport) will be stored for a maximum of 36 months after the last contact between the data subject and the data controller; This period is justified in order to engage with data subjects regarding any queries and/or follow up of the legal procedures. After 36 months of inactivity (and several notifications) the account and collected personal data will be automatically deleted;
- Contracts, data regarding payments and invoices are stored 10 years in order to comply with our legal responsibilities. This period is necessary in order to comply with applicable anti money laundering and tax law;
- All personal data collected from third parties will be deleted at the simple request of the user or ultimately after the expiration of the user account (after 36 months of inactivity). This period is justified on the basis of allowing the user to use collected data to exercise further rights (such as data portability or file complaints with the data protection authorities);
- When the account has been terminated by the users, all personal data and data regarding activities on the app, except the contracts and data regarding payments and invoices will be automatically deleted.
Evaluation: Acceptable
2.2 – Controls to protect the personal rights of data subjects
How are the data subjects informed on the processing?
The privacy statement of SOMI is published on the website https://somi.nl and will be directly accessible from the App.
Evaluation: Acceptable
If applicable, how is the consent of data subjects obtained?
When signing up, the explicit and informed consent of the data subjects will be asked. Whenever the data subject requests to process data collected from third parties, explicit and informed consent will be asked again. For example, when the data subject requests SOMI to exercise their right of access to a company, SOMI will ask the data subject to fill in the authorization letter and provide their signature. This authorization only valid per individual case, when the data subject wants SOMI to requests their data from another company, they should sign another authorization letter.
The consent regarding analytical data/cookies were provided on SOMI app and website. We employed the service of Cookiebot to that this process strictly adhere to the GDPR.
Evaluation: Acceptable
How can data subjects exercise their rights of access and to data portability?
Data subjects can make a request for data access and data portability by sending an email to privacy@somi.nl
Evaluation: Acceptable
How can data subjects exercise their rights to rectification and erasure?
Data subjects can make a request for data rectification and data erasure by sending an email to privacy@somi.nl
Also, in the App, functionalities will be added to for users to be able to permanently delete any data gathered from third parties.
Evaluation: Acceptable
How can data subjects exercise their rights to restriction and to object?
Data subjects can make a request for restriction and to object by sending an email to privacy@somi.nl
Evaluation: Acceptable
Are the obligations of the processors clearly identified and governed by a contract?
SOMI will ensure data processing agreements with the data processors. All data processors that come into contact with personal data will also be subject to a confidentiality agreement and informed about the responsibilities towards the rights of data subjects.
Evaluation: Acceptable
In the case of data transfer outside the European Union, are the data adequately protected?
All data will be stored in data warehouses located within the European Union. When third party SDK's are being used or (analytical) data is shared with data processors outside the EU, a risk assessment will be performed as per the Standard Contractual Clauses (SCC's).
Evaluation: Acceptable
Part 3 – Risk assessment
3.1 – Planned or existing measures
Supervision
The controller and data protection officer work closely together in order to monitor the effectiveness and adequacy of privacy controls. All new versions of the app will be subject to review by the data protection officer.
Evaluation: Acceptable
Personnel management
Only personnel with relevant assignments will be given access to personal data. All personnel that comes into contact with personal data will be subject to a confidentiality agreement and informed about the responsibilities towards the rights of data subjects.
Evaluation: Acceptable
Managing personal data violations
IT incidents and/or data breaches are logged in an internal incident register. For each incident, a severity impact assessment is performed and adequate measures to control, prevent and mitigate further incidents are implemented in close collaboration with management.
Evaluation: Acceptable
Integrating privacy protection in projects
For each important new project, a data protection impact assessment is made in close collaboration with management and IT support staff.
Evaluation: Acceptable
Organisation
SOMI is data controller and an independent Data Protection Officer has been appointed. Information security and data protection are discussed on a regular basis with all relevant parties within the organisation.
Evaluation: Acceptable
Physical access control
Access to the offices of SOMI is restricted to outsiders and controlled through use of an intercom with a camera.
Evaluation: Improvable
Action plan/corrective actions: Visitors should always be accompanied by an employee of SOMI.
Processing contracts
All data processors are required to sign data processing agreements. These contracts stipulate, in particular, measures regarding Article 32 (Security of processing), conditions regarding engaging sub-contractors and compliance with obligations regarding personal data breaches, data protection impact assessments and prior consultation.
Evaluation: Acceptable
Backups
Daily backups are made of all production data. Weekly backups of the entire database are stored at an external location (within the EU).
Evaluation: Acceptable
Website security
Annually, an external security audit of the website is performed. Adequate steps in order to improve security are discussed and implemented in close collaboration with management and IT support staff.
Evaluation: Acceptable
Clamping down on malicious software
Anti-malware software is installed on all workstations and servers with access to personal data.
Evaluation: Acceptable
Minimising the amount of personal data
SOMI aims to collect minimal data in order to achieve the stated purpose. Several measures have been taken in order to minimise the data collected:
- When asking for user identification, the user is requested to erase all special categories of data such as the photo, citizen service number and machine-readable zone. The user is recommended to use the 'Kopie ID' App provided by the Dutch Government in order to make a safe copy of his/her identification document.
- When collecting data from third parties, the data is automatically encrypted when first processed by SOMI. The user must provide explicit consent and his/her unique passphrase in order for any further processing of personal data to take place.
- After a period of inactivity, all collected personal data is automatically deleted (except data we are legally obliged to keep for a longer period of time).
Evaluation: Improvable
Action plan/corrective actions: When asking for a copy of the National ID, the data subject should black out passport photo, passport number, national ID number and machine-readable zone in this copy or photo.
Traceability (logging)
Currently, default logging of user activities is enabled on the server. Data regarding activities on the app and will be stored for a maximum of 12 months.
Evaluation: Improvable
Action plan/corrective actions: All activities on the server should be logged in order to retrieve information about data breaches.
Logical access control
Currently, access to the database is limited to a very small number of people. SOMI database is password protected and strictly logged. Any SOMI employee who needs access to information outside of their allocated role must log the request.
SOMI also uses 2-factor verification for both user and employee accounts for an extra layer of security.
Evaluation: Improvable
Action plan/corrective actions: Clear roles and permissions for users with access to the database should be defined.
Partitioning data
Currently, no partitioning of data is planned.
Evaluation: Improvable
Action plan/corrective actions: Partitioning measures should be implemented in order to prevent the entire database being leaked in case of a single security breach.
Anonymisation
Currently, no anonymisation mechanisms have been implemented since SOMI has the legal basis to process personal data.
Evaluation: Improvable
Action plan/corrective actions: Sensitive user information should be anonymised.
Encryption
All data ‘in transfer’ is encrypted using SSL. SOMI only encrypted the data provided by the third-party via subject access request. Only the user can access the readable format of those data.
Evaluation: Improvable
Action plan/corrective actions: In future versions of the App, all data collected from third parties should be encrypted using a stronger algorithm (AES-256) and complex user-generated key that is not available to the data controller. Whenever the data collected from third parties is processed, the data subject should be asked to give his/her user-generated key.
Hardware security
No data is stored on internal systems. External systems are secured with:
• Security: 24x7 staffed
• Cameras: HD infrared cameras
• Access control: badge and fingerprint system CERTIFICATIONS
• ISO Certified ISO 9001:2015 ISO 27001:2013
• PCI DDS compliant
Evaluation: Acceptable
Protecting against non-human sources of risks
All data is stored on Hetzner servers. These include the following measures:
POWER
• Rack feeds: separated A and B feed (32A)
• Diesel stock: 48+ hours, refillable during use
• UPS: 15+ minutes runtime
• Redundancy: N+2 COOLING
• Constant temperature: 21 Celsius
• Humidity: 50% (+/- 20%)
• Redundancy: N+2 FIRE PREVENTION
• Fire detection system: VESDA
• Fire suppression system: Argonite gas
• Redundancy: N+1
Evaluation: Acceptable
Policy
The data controller has been subject to an external GDPR audit and is in the process of implementing measures. All data processing activities are logged in an internal register of data processing activities.
Evaluation: Improvable
Action plan/corrective actions: Based on this Data Protection Impact Assessment, an information security plan should be rolled out prioritising the measures stipulated in the action plan (cf. infra).
Relations with third parties
All third-party relations who could come into contact with personal data are required to sign a non-disclosure agreement and data processing agreement.
Evaluation: Acceptable
3.2 – Risks
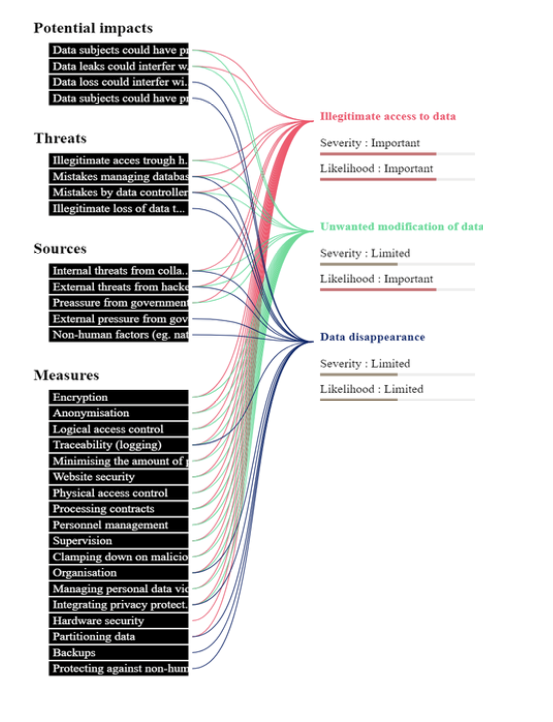
Illegitimate access to data
What could be the main impacts on the data subjects if the risk were to occur?
Data subjects could have private information shared with third parties. This could lead to moral as well as material damages for the data subjects. Data leaks could interfere with the exercising of the rights of data subjects
What are the main threats that could lead to the risk?
Illegitimate access through hacking, mistakes managing databases by collaborators, mistakes by data controllers
What are the risk sources?
Internal threats from collaborators, external threats from hackers or malicious parties, pressure from government agencies
Which of the identified planned controls contribute to addressing the risk?
Encryption, anonymisation, logical access control, traceability (logging), minimising the amount of personal data, website security, physical access control, processing contracts, personnel management, supervision, clamping down on malicious software, organisation, managing personal data violations, integrating privacy protection in projects, hardware security, partitioning data
How do you estimate the risk severity, especially according to potential impacts and planned controls?
Important, insufficient control measures have been taken to mitigate and/or control the risk of illegitimate access to data.
How do you estimate the likelihood of the risk, especially in respect of threats, sources of risk and planned controls?
Important, insufficient control measures have been taken to mitigate and/or control the likelihood of illegitimate access to data.
Evaluation: Improvable
Action plan/corrective actions: According to the available information, additional measures are needed to properly meet the requirements for protecting the data.
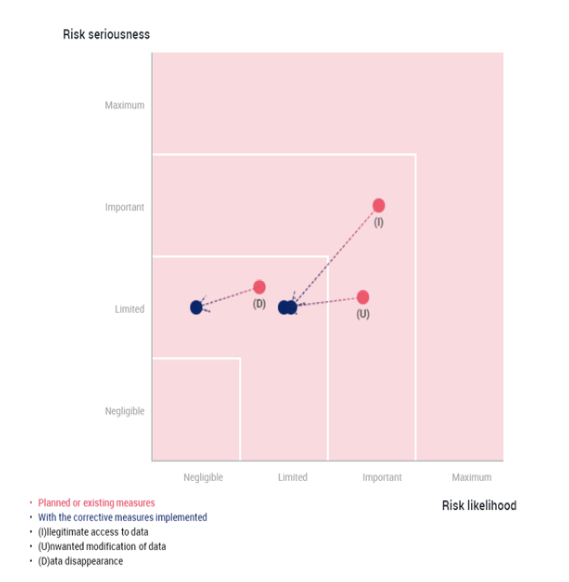
Taking into account the action plan, how do you re-evaluate the seriousness of this risk (Illegitimate access to data)?
Limited
Taking into account the action plan, how do you re-evaluate the likelihood of this risk (Illegitimate access to data)?
Limited
Unwanted modification of data
What could be the main impacts on the data subjects if the risk were to occur?
Data subjects could have private information shared with third parties. This could lead to moral as well as material damages for the data subjects. Data leaks could interfere with the exercising of the rights of data subjects
What are the main threats that could lead to the risk?
Illegitimate access through hacking, mistakes by data controllers, mistakes managing databases by collaborators
What are the risk sources?
External threats from hackers or malicious parties, internal threats from collaborators, pressure from government agencies
Which of the identified controls contribute to addressing the risk?
Supervision, personnel management, managing personal data violations, integrating privacy protection in projects, organisation, physical access control, processing contracts, website security, clamping down on malicious software, minimising the amount of personal data, traceability (logging), logical access control, anonymisation, encryption
How do you estimate the risk severity, especially according to potential impacts and planned controls?
Limited, Adequate control measures have been taken to mitigate and/or control the risk of unwanted modification of data.
How do you estimate the likelihood of the risk, especially in respect of threats, sources of risk and planned controls?
Important, insufficient control measures have been taken to mitigate and/or control the risk of unwanted modification of data.
Evaluation: Improvable
Action plan / corrective actions: According to the available information, insufficient measures have been taken to mitigate and/or control the risk of modification of data.
Taking into account the action plan, how do you re-evaluate the seriousness of this risk (Unwanted modification of data)?
Limited
Taking into account the action plan, how do you re-evaluate the likelihood of this risk (Unwanted modification of data)?
Limited
Data disappearance
What could be the main impacts on the data subjects if the risk were to occur?
Data loss could interfere with the exercising of the rights of data subjects, data subjects could have private information lost
What are the main threats that could lead to the risk?
Illegitimate loss of data through hacking, mistakes by data controllers, mistakes managing databases by collaborators
What are the risk sources?
External threats from hackers or interested parties, internal threats from collaborators, external pressure from government agencies, non-human factors (e.g. natural disasters)
Which of the identified controls contribute to addressing the risk?
Integrating privacy protection in projects, organisation, backups, traceability (logging), partitioning data, protecting against non-human sources of risks.
How do you estimate the risk severity, especially according to potential impacts and planned controls?
Limited, Adequate control measures have been taken to mitigate and/or control the risk of disappearance of data.
How do you estimate the likelihood of the risk, especially in respect of threats, sources of risk and planned controls?
Limited, Adequate control measures have been taken to mitigate and/or control the likelihood of disappearance of data.
Evaluation: Improvable
Action plan / corrective actions: According to the available information, adequate measures have been taken to mitigate and/or control the risk of data disappearance.
Taking into account the action plan, how do you re-evaluate the seriousness of this risk (Data disappearance)? Limited
Taking into account the action plan, how do you re-evaluate the likelihood of this risk (Data disappearance)? Negligible
3.3 – Risk mapping
Risks - Illegitimate access to data
Action plan/corrective actions: According to the available information, additional measures are needed to properly meet the requirements for protecting the data.
Taking into account the action plan, how do you re-evaluate the seriousness of this risk (Illegitimate access to data)? Limited
Taking into account the action plan, how do you re-evaluate the likelihood of this risk (Illegitimate access to data)? Limited
Risks - Unwanted modification of data
Action plan/corrective actions: According to the available information, adequate measures have been taken to mitigate and/or control the risk of modification of data.
Taking into account the action plan, how do you re-evaluate the seriousness of this risk (Unwanted modification of data)? Limited
Taking into account the action plan, how do you re-evaluate the likelihood of this risk (Unwanted modification of data)? Limited
Risks - Data disappearance
Action plan/corrective actions: According to the available information, adequate measures have been taken to mitigate and/or control the risk of data disappearance.
Taking into account the action plan, how do you re-evaluate the seriousness of this risk (Data disappearance)?
Limited
Taking into account the action plan, how do you re-evaluate the likelihood of this risk (Data disappearance)?
Negligible
3.4 – Action plan
Physical access control
Action plan/corrective actions: Visitors should always be accompanied by an employee of SOMI.
Minimising the amount of personal data
Action plan/corrective actions: In the current version, the App requests a full copy of the National ID for ID verification (cf. app purchase workflow). When asking for a copy of the National ID, the data subject should be requested to blackout passport photo, passport number, national ID number and machine-readable zone in this copy of photo.
Traceability (logging)
Action plan/corrective actions: All activities on the server should be logged in order to allow digital forensics in case of a data breach.
Partitioning data
Action plan/ corrective actions: Partitioning measures should be implemented in order to prevent the entire database of being leaked in case of a single security breach.
Anonymisation
Action plan/ corrective actions: Sensitive user information should be anonymized.
Encryption
Action plan/corrective actions: All data collected from third parties should be encrypted using a strong algorithm (AES-256) and complex user-generated key that is not available to the data controller. Whenever the data collected from third parties is processed, the data subject should be asked to give their user-generated key.
Policy
Action plan/corrective actions: Based on this Data Protection Impact Assessment, an information security plan should be rolled out prioritizing the measures stipulated in the action plan (cf. infra).
Part 4 – Validation
DPO opinion
DPO's name
Koen Hostyn koen@privacyforall.be
DPO's opinion
Provided the technical and organisational measures described in the PIA are implemented correctly, I give a favorable advise for the data processing in question, taking into account the following recommendations for future releases of the App:
- • Remove HSM Core as a standard component from the App, due to the risks associated with data transfers outside of the EEA, in particular to Singapore and China.
- • Verify the processing of data by Google is set to ’anonymize IP’ and provide the user with an opt-out function for sharing any personal data with Google.
- • Verify the transfer mechanism OneSignal relies on to transfer data outside of the EEA, and ensure informed user consent is granted before any data is shared with OneSignal.
- • Perform an external independent penetration test before any new major release of the App (as recommended before).
- • Consult the DPO and perform a privacy by design – assessment whenever new categories of personal data are being processed by the App.
Search of concerned people opinion
A debug version of the App was submitted to a number of peers of SOMI for feedback, however a concerned people opinion consultation has not been performed.
Any additional questions or concerns can be submitted to privacy@somi.nl